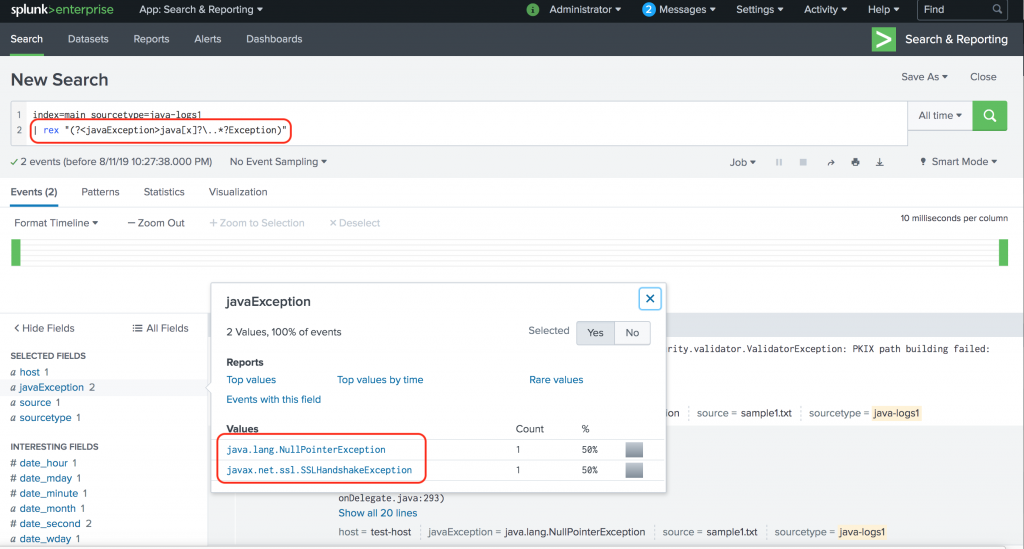
Splunk is a powerful platform that allows organizations to analyze and visualize their machine-generated data in real-time. One of the key features of Splunk is its ability to extract fields from raw data using regular expressions, also known as regex. In this article, we will dive deep into the world of Splunk field extraction regex and explore how it can be optimized to improve data analysis and reporting. Field extraction in Splunk is the process of identifying and extracting specific pieces of data from raw logs or events. These fields can be used to create meaningful and actionable insights from the data. Splunk provides a variety of methods to perform field extraction, including automatic field discovery, interactive field extraction, and regex-based field extraction. Regex is a powerful pattern matching language that allows you to define complex patterns to search for and match specific strings in your data. Splunk leverages regex to extract fields by defining patterns that match the desired data. The extracted fields can then be used for further analysis, filtering, and reporting. To optimize Splunk field extraction using regex, it is important to understand the structure and format of the data you are working with. By having a clear understanding of the data, you can create more precise regex patterns that accurately extract the desired fields. This can help reduce false positives and improve the accuracy of your field extraction. Here are some tips to optimize Splunk field extraction regex: 1. Use Anchors: Anchors are regex characters that define the start and end of a line or string. By using anchors, you can ensure that your regex pattern matches the desired field within a specific context. For example, if you want to extract a field that always appears at the beginning of a line, you can use the "^" anchor to match the start of a line. 2. Use Quantifiers: Quantifiers allow you to specify the number of times a character or group of characters should appear in your regex pattern. By using quantifiers, you can create more flexible and efficient regex patterns. For example, if you want to extract a field that consists of a sequence of digits, you can use the "d+" quantifier to match one or more digits. 3. Use Character Classes: Character classes allow you to specify a set of characters that can match a single character in your regex pattern. By using character classes, you can create more precise and readable regex patterns. For example, if you want to extract a field that consists of alphanumeric characters, you can use the "[a-zA-Z0-9]+" character class to match one or more alphanumeric characters. 4. Use Capturing Groups: Capturing groups allow you to create subpatterns within your regex pattern and extract specific parts of the matched string. By using capturing groups, you can extract multiple fields from a single regex pattern. For example, if you want to extract a field that consists of a username and domain, you can use the "([a-zA-Z0-9]+)@([a-zA-Z0-9]+)" capturing group to match and extract the username and domain separately. 5. Use Lookaheads and Lookbehinds: Lookaheads and lookbehinds are zero-width assertions that allow you to match a pattern only if it is followed or preceded by another pattern, without including the lookahead or lookbehind in the actual match. By using lookaheads and lookbehinds, you can create more complex and efficient regex patterns. For example, if you want to extract a field that appears after a specific string, you can use the "(?<=specific_string)regex_pattern" lookbehind to match the field only if it is preceded by the specific string. 6. Use Non-Greedy Quantifiers: By default, quantifiers in regex are greedy, meaning they match as much as possible. However, in some cases, you may want to match as little as possible. By using non-greedy quantifiers, you can create more precise regex patterns. For example, if you want to extract a field that appears between two specific strings, you can use the "(?<=start_string).*?(?=end_string)" non-greedy quantifiers to match the field between the start and end strings. 7. Test and Iterate: Field extraction regex can be complex, and it often requires trial and error to get it right. It is important to test your regex patterns against sample data and iterate until you get the desired results. Splunk provides a regex tester tool that allows you to test your patterns and see the extracted fields in real-time. Take advantage of this tool to fine-tune your regex patterns. In conclusion, optimizing Splunk field extraction regex is crucial for accurate and efficient data analysis in Splunk. By understanding the structure and format of your data, using anchors, quantifiers, character classes, capturing groups, lookaheads, lookbehinds, non-greedy quantifiers, and testing and iterating, you can create regex patterns that accurately extract the desired fields. This will help you gain valuable insights from your data and make informed business decisions.
How to use regex in field extraction? - Splunk Community. Solved: I cant seem to get my regex to work as a field extraction. below is an example string and the regex Im trying to use. Sample SplunkBase Developers Documentation splunk field extraction regex. About regular expressions with field extractions - Splunk splunk field extraction regex. You can use the field extractor to generate field-extracting regular expressions. For information on the field extractor, see Build field extractions with the field extractor . Proper field name syntax Field names must conform to the field name syntax rules splunk field extraction regex. Valid characters for field names are a-zA-Z0-9, . , :, and .. Solved: Field Extraction Using Regex - Splunk Community. Field Extraction Using Regex MaddyRaj Engager yesterday I have 2 requests here. I am trying to extract and create a new field from logs. Logs for request 1:. How to create a regex to extract data? - Splunk Community splunk field extraction regex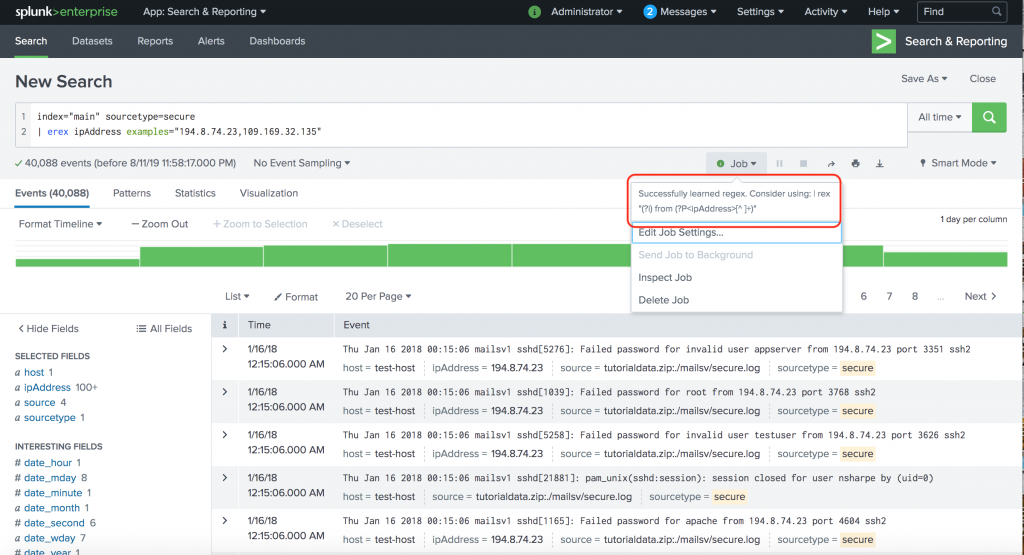
pamper parties for girls sydney
. Extract fields with search commands - Splunk Documentation. Extract fields using regular expressions The rex command performs field extractions using named groups in Perl regular expressions that you include in the search criteria. The rex command matches segments of your raw events with the regular expression and saves these matched values into a field. splunk field extraction regex. Solved: Re: Rex field extraction - Splunk Community. The best way to extract structured data is spath. If for some reason log is not available as a field, you should extract the full JSON object that contains "log" as a key, extract that JSON with spath, then extract fields contained in log using spath. log is not available as a field splunk field extraction regex. Solution didnt work. splunk field extraction regex. regex - Splunk Documentationgay dating sites australia
. Use the rex command to either extract fields using regular expression named groups, or replace or substitute characters in a field using sed expressions. Using the regex command with != If you use regular expressions in conjunction with the regex command, note that != behaves differently for the regex command than for the search command.how long does a cock need to be to fuck doggie style
. About calculated fields - Splunk Documentation
best sports sweepstakes
. Use calculated fields as a shortcut for performing repetitive, long, or complex transformations using the eval command
sheetz westchester high point nc
. You can have the field extractor generate a field-extracting regular expression, or you can employ delimiter-based field extraction splunk field extraction regex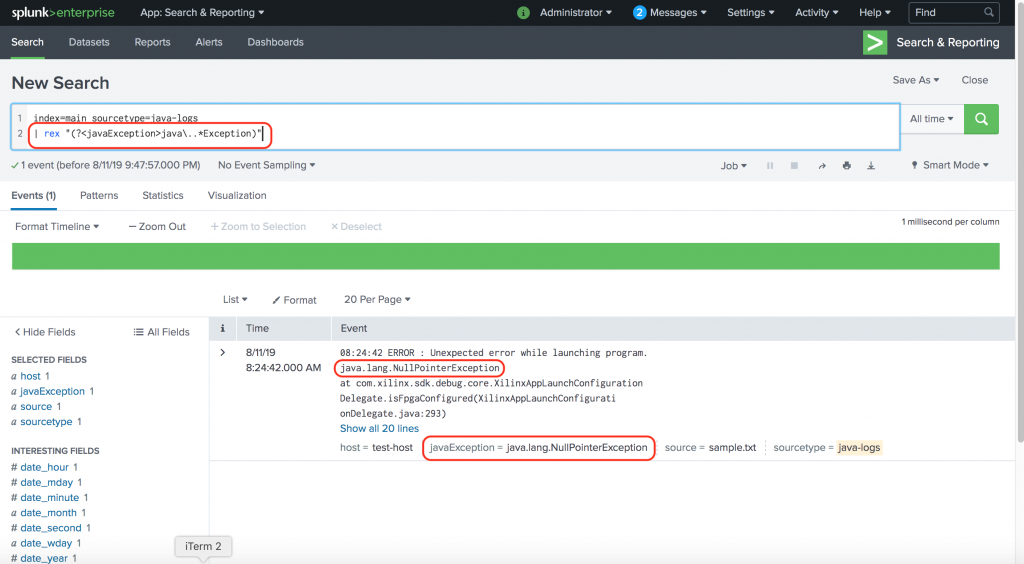
tell me you want to fuck
. Regular Expressions in Splunk | Splunk Fields | Splunk Field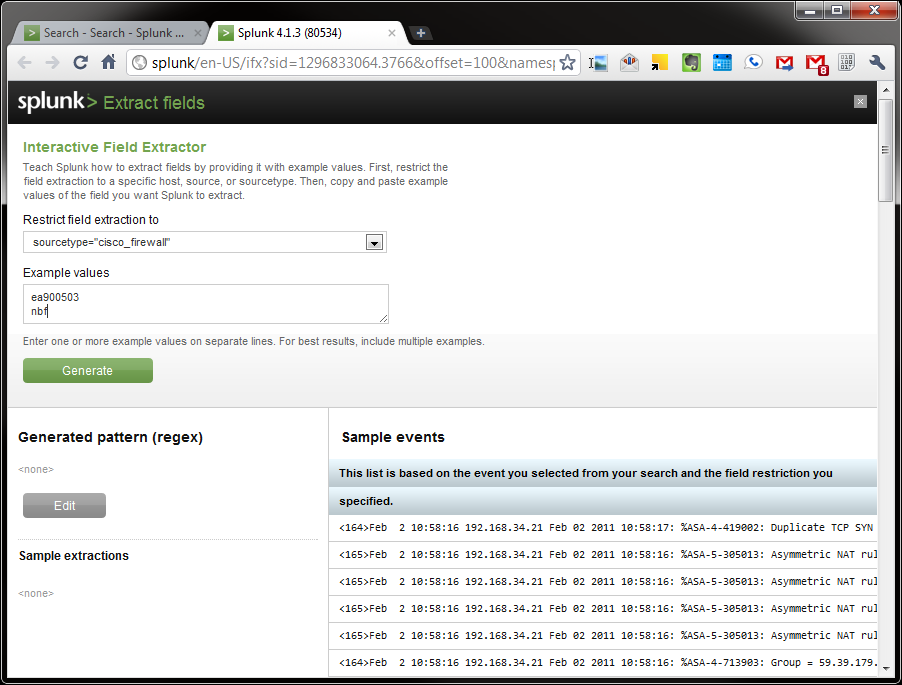
coleman 100cc mini bike top speed
. | rex " (?<user_domain>w+@w+)" Or you could make this kind of extraction permanent by using the interactive field extractor ( ocs.splunk.com/Documentation/Splunk/latest/User/InteractiveFieldExtractionExample ).. Splunk > Field Extraction - LinkedIn. Field extraction is a powerful feature of Splunk that can help you better organize and analyze your data. With regular expressions, you can extract specific fields from your data and make it .pic quote today i woke up like fuck you
. Solved: Regex field extraction - Splunk Community. Solved: Regex field extraction - Splunk Community Solved: Hello all, I have one sourcetype that does not allow me to create a static field extraction, because we have several fields with different COVID-19 ResponseSplunkBaseDevelopersDocumentation Browse Community Community Splunk Answers Splunk Administration Deployment Architecture Installation. How to use rex command to extract fields in Splunk?. In this article, Ill explain how you can extract fields using Splunk SPLs rex command. Ill provide plenty of examples with actual SPL queries splunk field extraction regex. In my experience, rex is one of the most useful commands in the long list of SPL commands